|
The Options button displays the Options window Tabs where you configure your
individual custom set-up.
Three basic classes of secure cleaning processes are available: File, Folder and
Registry operations. A legend is included at the lower left of the window
indicating which is which. Some options go beyond the basic specification
and target more involved specific known areas where evidence can be stored on
your computer.
The Windows Options Tab provides control over four areas of concern. General
history data files recorded by Windows such the Swap File, Computer user
activity logs, the Windows clipboard functions, and other areas as shown below.
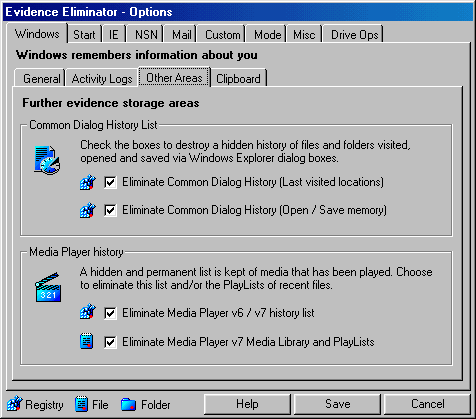
The following secure Windows history cleaner options are available:
 | Windows SWAP File |
 | Windows Temporary History Files |
 | Windows PC User Profiles |
 | Windows Registry Streams |
 | Windows Application History Logs |
 | Common Dialog History List |
 | Media Player History |
 | Media Player v7 Media Library and Playlists |
 | Windows Clipboard Memory |
MAIN MENU
There is a hidden encrypted database in the system registry which remembers a
wide range of Windows history information about what you have clicked on your start menu. The
dates and times of mouse clicks are stored with the names of programs started. This
option will clear and erase Start Menu History database and eliminate all the entries from
it.
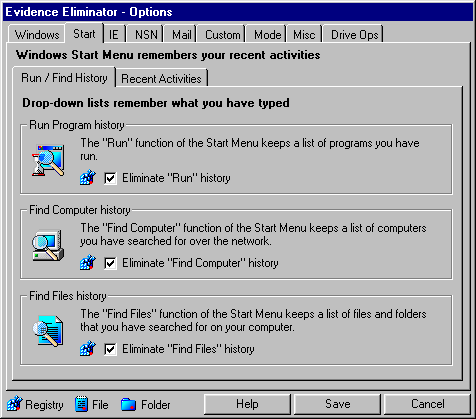
The Start tab will erase various history lists from your Windows Start Menu:
 | Run Program History |
 | Find Computer History |
 | Find Files History |
 | Recent Documents List |
 | Start Menu Order History |
 | Start Menu Click History |
MAIN MENU
Evidence Eliminator runs as a secure Internet History and Cookies
Eraser. The IE tab contains configuration settings for Internet Explorer
browser users, and the NSN tab contains settings for Netscape Navigator
browser users.
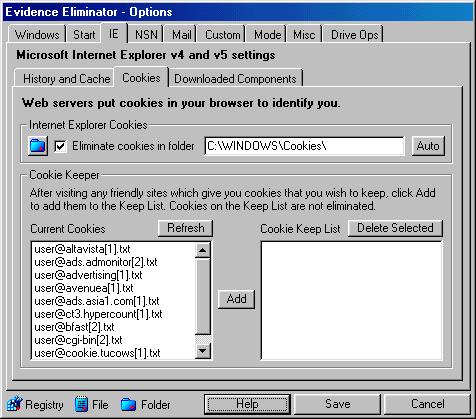
Internet Explorer [IE] Options Tab targets the following items for erasing:
 | Internet History and Cache Eraser Tab |
 | Internet Explorer Typed URL's |
 | Internet Explorer AutoComplete |
 | Internet Explorer Download Folder memory |
 | Internet Explorer URL Error Logs |
 | Internet Explorer Cache |
 | aka Temporary Internet Files |
 | Internet Explorer Cache (Local Settings) |
 | Internet Explorer Favorites (URL Bookmarks) |
 | Internet Explorer Visited URL History |
 | Internet Explorer Cookies Eraser |
 | Downloaded Components Tab |
 | Internet Explorer Downloaded Program Files |
Netscape Navigator [NSN] Options Tab targets similar items as above for
secure file erasing. Please see the program Help file for more information.
MAIN MENU
This section allows you to securely erase Email and News Message history
stored within programs and hidden Windows files. This includes email and
newsgroup
activities under Outlook Express v5/v6, Internet Explorer v5/v6 or Netscape
Navigator v3/v4.
Evidence Eliminator™ v5 offers full control over the hidden database
files stored by Outlook Express to erase email folders and selected news message
history databases.
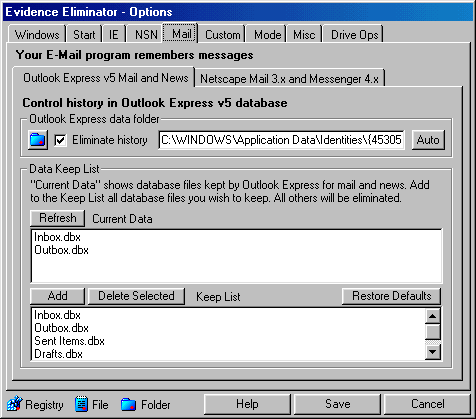
The Evidence Eliminator Erase Email News Message Options Tab targets
the following items to securely erase:
At the top of this option, the erase function can be switched on or off, and the
email/news storage folders selected. An
"Auto" button is provided to detect the file folder locations automatically. On
new Windows installations, the "Auto" button will not work until you
have set up an e-mail account in Outlook Express.
Two windows are provided listing database files. The upper window lists all
database files currently kept by Outlook Express. Select an item in the upper
list and press "Add" to add it to the lower window - the "Keep
List".
When you run Evidence Eliminator™, it will delete/erase everything in
Outlook Express except those items on the lower Keep List.
The default settings may be restored with the "Restore Defaults"
button. The defaults keep Inbox, Outbox, Drafts, Sent and Deleted items.
Most email/news database file names will appear self-explanatory for the various mail
folders and newsgroups which you use. The file "Pop2uidl.dbx" can be safely deleted/erased.
"Folders.dbx" contains lists of newsgroups available on servers and
may contain other information about which groups have been read. If in doubt
erase/delete it, but you will have to re-download the news groups list when you log on next
time.
Your account information (passwords, internet mail and news server accounts,
names, e-mail addresses that you use) are not affected by this function.
They are stored in the system registry and changed from the Outlook Express
"Tools - Accounts" menu.
It is advisable to run "Compact" from the File Menu of Outlook
Express to remove old data file traces of sent and deleted emails from the main database,
before running Evidence Eliminator™.
MAIN MENU
Netscape E-Mail 3.x and Messenger 4.x
Check the top two boxes according to the Netscape E-Mail versions installed on
your computer. Ensure that the folder paths listed point to the Mail folder in
your Netscape installation.
Netscape Email "Hidden Files" - security hole.
The ".snm" files created by Netscape Communicator Mail v4.6 (and
possibly other versions) are seriously insecure and can store and preserve
megabytes of information from your hard drives which are nothing whatsoever
related to E-Mail. These files are allegedly certified disposable by Netscape
support and this does not interfere with the operation of Netscape. Evidence
Eliminator™ will erase/destroy them for you automatically.
Netscape Mail History
Enable this option to erase copies which Netscape keeps of your sent and
deleted email messages. It will not delete folders from the trash. If you
delete any folders when configuring Netscape Mail, remove them manually from the
trash.
Netscape Email Security Hole #2
After you use Netscape Mail, select "Compact folders" from the
menu. On our test version (4.73) this function often fails and leaves copies of
sent emails hidden in the database. Our advice if you are concerned about
email security is to use Microsoft Outlook Express instead.
MAIN MENU
The Custom Tab is used to set up the hard drive cleaner functions to
erase or save specific files, file contents, folders and special program
history records.
Special software Plug-ins have been included in Evidence Eliminator
to target various popular programs, and they also provide a Custom Plug-in
Tool that allows you to create individual plugins for specific programs
you may be running on your own computer.
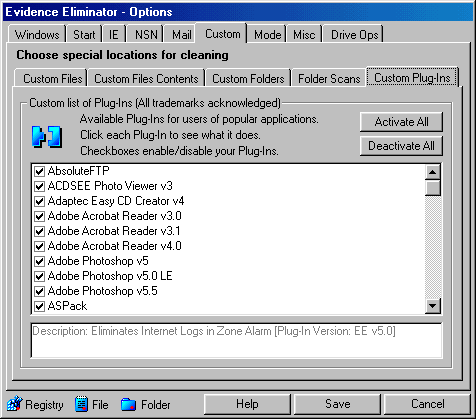
The custom file cleaner, folder scans, and plug-ins Options Tab targets the
following items for erasing:
 |
Custom Files Cleaner
 |
Enter here individual files which you wish to be processed and
deleted. |
|
 |
Custom Files Content Cleaner
 |
Enter here individual files which you wish to be processed without being
deleted. The file will remain in the same place on the disk with contents
securely erased and deleted. This section only deals with individual known
files. It does not scan for files matching patterns. |
|
 |
Custom Folders Cleaner
 |
All folders you list here will be securely cleaned, erased and deleted. Any files within them
will be erased/deleted, and any sub-folders inside, and their contents, will also be
erased/deleted. |
|
 |
Folder Scans File Cleaner
 |
All folders you list here will be scanned with the specified file masks. |
 |
This function is identical to the Drive Scan except it allows you to target
individual folders and file types. An example: To delete all .log files in c:\test\
you would enter c:\test\ in the folder section and
enter *.log in the mask section. |
|
 |
Custom Plug-Ins Program File Cleaner
 |
All Evidence Eliminator™ Plug-Ins available are listed for popular
applications. Check the boxes on the left to enable or disable each Plug-In and
read their descriptions below. For complete information about Plug-Ins, read the
main Plug-Ins Help Page. |
|
MAIN MENU
If you use Chat programs, view your Program Files
directory for any files they keep. If logs are being kept simply add the full path of the
log file to the "Custom Files" list in the Options window, and they
will be subjected to the standard data destruction process automatically.
IRC Chat users may add their download folder to the
list of "Custom Folders" to guard against any uninvited files put
there by other users.
MAIN MENU
Select your choice of secure file eraser/destruction methods. In Windows mode, you
can if you wish set up file deletion similar to the U.S. Government Department
of Defense DOD Standard 5220.22-M. Even in
the lowest security setting, Evidence Eliminator securely destroys data and the chance
of recovery of evidence is practically zero.
Windows - Method Of Destruction
Zero - The file is over-written with zero's. (00000000)
Zero + Reverse - As above but then overwritten with 1's (11111111)
Zero + Reverse + Randomize - As above, but then overwritten with
pseudo-random garbage
Windows - Repetitions of Destruction
The above process can be repeated up to nine times. If you enter Zero +
Reverse with 2 repetitions, that multiplies to 4 overwrites (Zero, Reverse,
Zero, Reverse)
and the two passes will appear in the activity log as: <P1>[0][-]<P2>[0][-]
Windows - Extra Security Countermeasures
By scrambling the file's name and size before deleting it, you can add
another layer of security against snoops.
It is also possible to choose "Standard" insecure deletes if speed
of deletion is the most important requirement.
DOS Mode - Select Repetitions
In DOS Mode, a different and simpler system is used. You can select up to 9
overwrites and those overwrites will alternate between Zero and Reverse at each
pass. Securely overwriting just once will practically destroy data so that forensic
software cannot recover any evidence from your hard drives.
MAIN MENU
This Evidence Eliminator Options Tab contains miscellaneous
secure cleanup functions and control settings, including the
Windows Registry functions, Program Control and Stealth Mode Tabs.
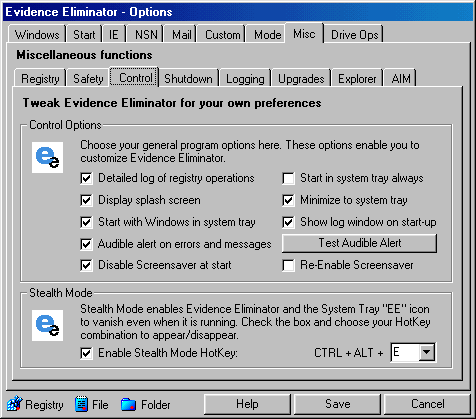
The Miscellaneous Computer cleanup Options Tab offers the following user control functions and
targets the following items for erasing:
 |
Windows Registry Backups |
 |
Cleanup and Repair Registry with
RegClean |
 |
Defragment Registry |
 |
Program Control cleanup functions |
 |
Stealth Mode hidden operations |
 |
Shutdown Interception |
 |
Program Logs cleanup options |
 |
Automatic Program Update checking |
 |
Windows Explorer (Right Click Context Menu commands) |
 |
Shell Extensions switch for Stealth Mode |
MAIN MENU
The Drive Ops Options Tab provides various specific hard drive
disk cleanup eraser functions in a centralized format,
beginning with the Drive List Tab.
 | Drive List - central list of hard drives on the system. |
 | Drive Scan Functions - special file types to cleanup/erase |
 | Enable File Scanning - switches the function on or off. |
 | File Masks - wild card patterns the drives will be scanned
for |
 | High-Performance Mode Functions |
In High performance mode, two functions are available - high-speed cleaning
of directory structures and high-speed cleaning of file cluster tips.
When you delete files, Windows sometimes keeps their names buried in the
directory structure of the hard drive. This function scans and analyzes all the
folders on your drives, securely erasing all traces of deleted file names,
and also their times, dates, sizes and attributes, leaving not one single trace
of evidence remaining. As a full low-level cleaning solution, it is activated by
a single checkbox. There is no need to adjust this function in any way, it is
fully automatic.
Files are stored on your disk in clusters. Clusters are fixed chunks of space
provided by the Windows File System. If the cluster size is 4kb and your file is
6kb, then your file takes two clusters but only occupies half the second
cluster. Files normally have free space at their tips, containing data left-over
from previous insecurely deleted files.
Evidence Eliminator™ automatically scans all your drives, analyzes
each individual file and securely overwrites [erases] the cluster tip space with multiple
passes of garbage according to your settings under the Mode
Tab. There is no commercial service available that can reverse this function
- total elimination.
Evidence Eliminator™ will cleanup/erase the cluster tips
of all files, including system files and DLL's - even while Windows has the
files "locked" - Evidence Eliminator™ will still clean them
for you.
The disk space beneath
existing files and folders can be securely overwritten with multiple passes of
garbage according to your settings under the Mode
Tab to defeat hardware analysis of deleted files by
electron microscopes!
Within each file and folder in your disk, a variety of date and time
information is stored. You can see some (but not all) of this information by
right-clicking on files or folders in Windows explorer and selecting
"Properties". In addition to Date and Time of creation, modification
and date of last access, each file also remembers a hidden counter of Centi-Second
(one-hundredths of one second) accuracy, showing when the file was made.
This option enables Evidence Eliminator™ to completely scramble
these records as it performs the "Securing Directory Structures"
operation.
Randomizing into the future a month or two provides "cover" even
after you have finished running EE. Because any dates or times of any file
accesses you make, are "smoke screened" by the randomized dates and
times you have already created in the future. It's impossible to prove which
files were dated because you used them, and which files were dated because of
the randomization process of Evidence Eliminator™.
This provides effective cover against snoops analyzing the date and time
records of the files and programs in your PC.
An essential function to make sure you complete the job properly. Don't skimp
on this section. It takes a little time.
Enable Hard Drive Free Space Elimination
Free data in all unallocated areas on your drive is overwritten with multiple
passes of garbage according to your settings under the Mode
Tab. There is no commercial service available that can reverse this function
- total elimination.
MAIN MENU

A Lifetime Of Protection
As a Licensed User you are entitled to use Evidence Eliminator™ on a
permanent basis. This includes free lifetime Technical Support and you are
entitled to obtain and activate all future upgrades on this product for free!
You do not have to pay again!
You may install multiple copies of the program as long as only the specified
number of Licensed copies is in use at one time. For example on a Single-User license, you may
install the program at work, at home and on your laptop, as long as only a Single copy of the
software is in use at one time.
To install additional copies of Evidence Eliminator™ to each PC, simply download
from the Website and use your existing Key Codes to activate the License on the
new installation.
[ Back to Top ] |